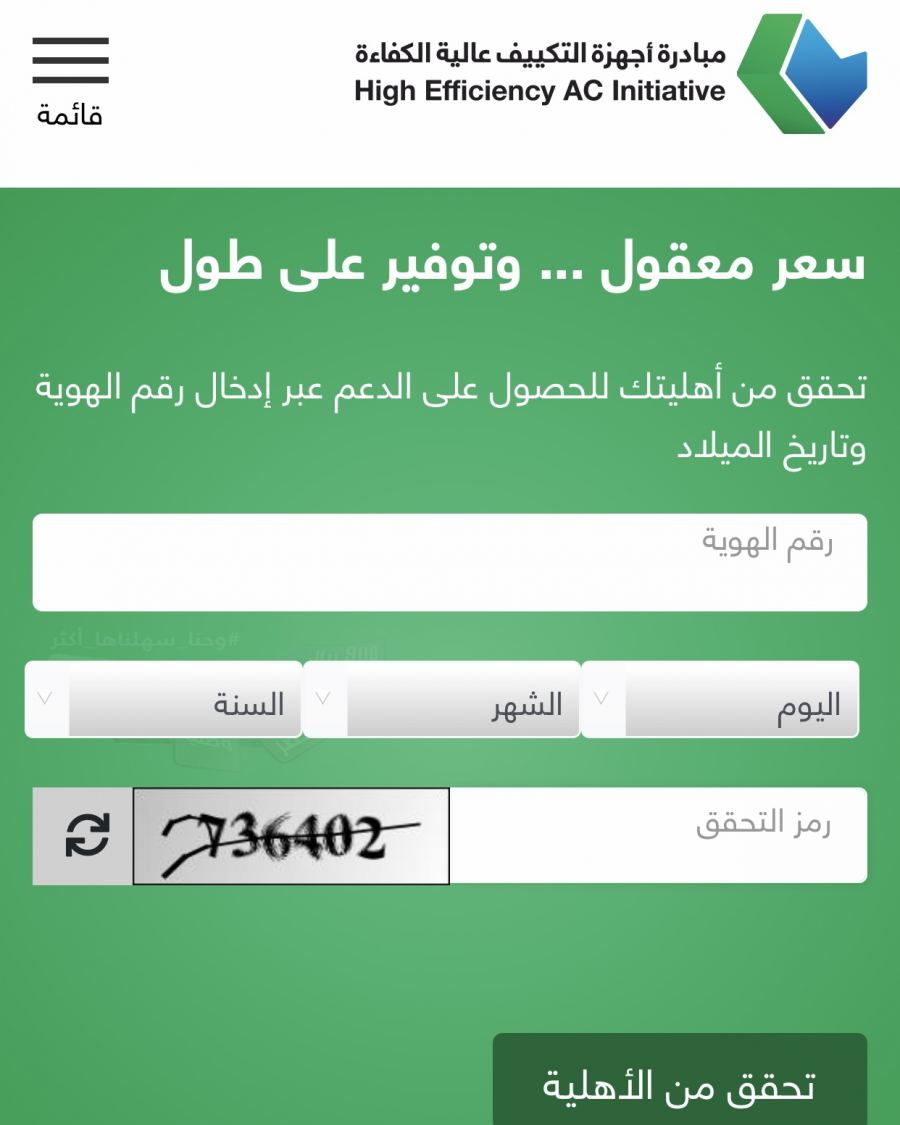
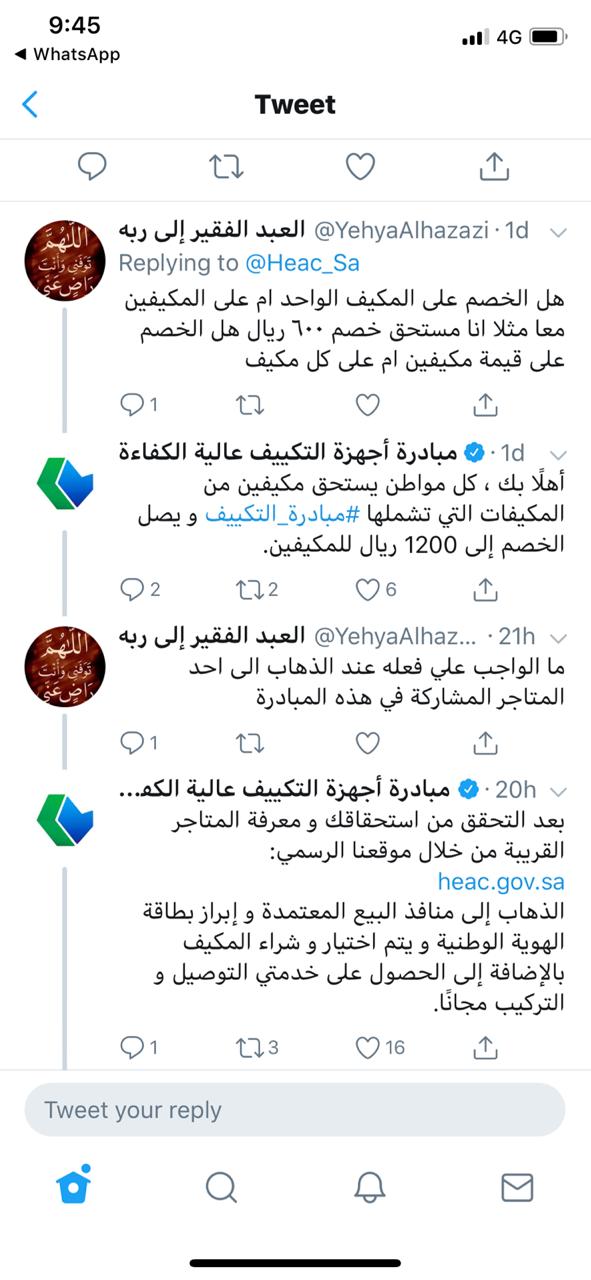
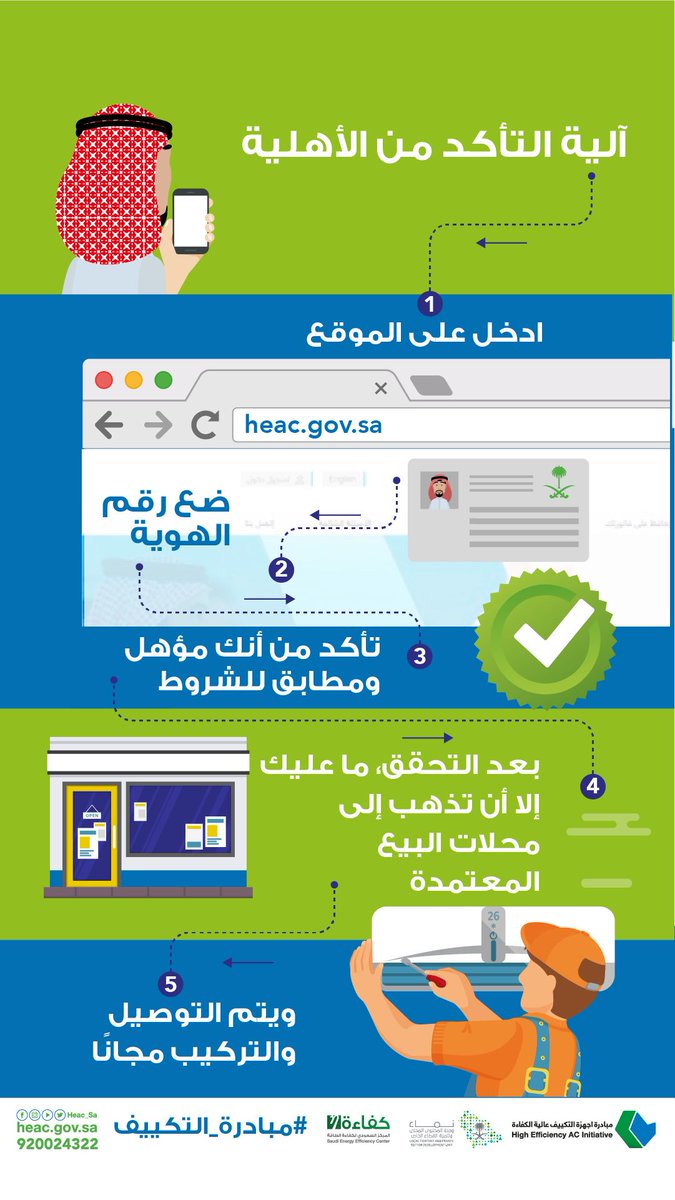
عبدالله الرشيد auf Twitter: "مبادرة حكومية لدعم المسجلين بحساب المواطن 👍 يعطونك خصم عند شراء عدد 2مكيف خصم 400ريال على مكيف 18 ألف وحدة وخصم 600 على مكيف24 ادخل هنا : https://t.co/1qhsJX6gEM

العروض 🏷️ Twitterissä: "مبادرة حكومية لدعم المسجلين بحساب المواطن أو من عمره فوق 24 سنة من شراء عدد 2 مكيف كحد أقصى بدعم قيمته 600 ريال لكل مكيف الطريقة: ادخل على الرابط